
A story broke today on social bookmarking sites The Hacker News and Reddit that Facebook was blocking access to people trying to log in to their account using the anonymity software Tor.
As it turns out Facebook wasn’t intentionally doing this, and a post on Tor’s blog explained what had happened.
“A number of users have noticed that Facebook is blocking connections from the Tor network. Facebook is not blocking Tor deliberately. However, a high volume of malicious activity across Tor exit nodes triggered Facebook’s site integrity systems which are designed to protect people who use the service. Tor and Facebook are working together to find a resolution.”
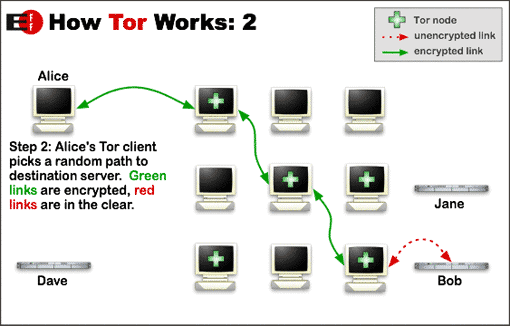
Tor, an acronym for The Onion Routing Project, blocks access to any individual user’s location by directing traffic through a free, worldwide volunteer network consisting of thousands of relays that encrypt and re-encrypt data multiple times. The software launched more than a decade ago, but has become more popular of late because it has become a key tool to those involved in Arab Spring protests.
Two years ago The Tor Project was awarded the Free Software Foundation’s 2010 Award for Projects of Social Benefit on the following grounds. The foundation explained the reasoning behind the prize.
“Using free software, Tor has enabled roughly 36 million people around the world to experience freedom of access and expression on the Internet while keeping them in control of their privacy and anonymity. Its network has proved pivotal in dissident movements in both Iran and more recently Egypt.”
The use of social has been considered a key factor to those observing protests in places like Libya, Egypt and Syria, and Tor’s rise has paralleled the increasing use of Twitter and Facebook as people look to communicate anonymously on popular platforms.
Phillip Howard, author of “Democracy’s Fourth Wave?: Digital Media and the Arab Spring” says this is a historic development.
“There was a longstanding democracy movement in these countries that for many years tried many tactics but none of them worked,” says Howard. The University of Washington communications professor says Arab Spring movements that “involved a networked public of generally younger folks” were different than previous movements that were centered around a charismatic leader.
But is Tor absolutely secure? That is an issue of some debate. Several groups have claimed successful attacks against the network, including French researchers from National Institute for Research in Computer Science and Control, who claimed to have documented an attack capable of revealing the IP addresses of BitTorrent users using Tor.
In May, the Australian Attorney-General’s Department has claimed it would be “trivially easy” for its intelligence services to break into Tor.
But Tor developer Jacob Appelbaum says this would not be possible, in part because the network’s encryption keys are temporary and not know even to system operators. Applebaum scolded those who might try to break Tor’s encryption, and clarified why he thinks Tor is an important social tool.
“I’m sorry to hear that Australian politicians are interested in joining the ranks of China, Russia, Iran and Belarus to name a few,” he said about the Attorney-General’s claims.
Applebaum said such efforts would be counter-productive to society as a whole.
“If they wish to break such services, they ensure that when they use such services, they will also be insecure this ensures again that only criminals will have privacy, regular people, including the police fighting crime they will be left out of having strong privacy. This opens business people up to industrial and economic espionage. It also promotes the idea that to make ourselves more secure, we should weaken our networks and add the very backdoors that most attackers work day and night to create,” he said.
“This isn’t just a civil liberties argument, I might add though to be free from suspicion is a key part of the civil liberties battle. This is a matter of economic security as well as national security. Data retention presents a very large attack surface and the larger the attack surface, the more valuable the target, the more damage an attack will rain down on those impacted by such data retention. This is true for surveillance and censorship as much as the data collected from such systems. This in itself is threat to national security when an attacker may know what every politician, every kid, every business person what everyone is doing and thinking online.”
Comment
One thought on “A primer on Tor, the software that is encrypting the Arab Spring”
Leave a Reply
You must be logged in to post a comment.





 Share
Share Tweet
Tweet Share
Share



Good work, Tor is currently undergoing a attack hosted by the FBI theory was entirely too correct.