
 This report was adapted by Cantech Letter from a piece prepared by the Virtus Advisory Group, Inc.
This report was adapted by Cantech Letter from a piece prepared by the Virtus Advisory Group, Inc.
The commercialization of the internet since the 1980’s has continuously and exponentially changed the way of the modern world. This applies to both consumers and businesses alike. On the consumer end, unlimited information is available at the touch of a button. Everyday tasks that used to take time and effort like depositing money in the bank are now as simple as taking a picture with a mobile device and entering your banking information online. From an industry viewpoint, technology creates the opportunity to reach a much wider marketplace and continuously offer new products and solutions to consumers which helps firms not only stay relevant in an ever-changing landscape, but also find new ways to grow revenues.
As a result of this paradigm shift, data collection has become an essential component of many business operations. Whether it be the collection of customer information or of internet cookies, the storage of data couldn’t be more important. Naturally, as the necessity for efficient data collection grows, so does the need to protect that information at all costs.
It doesn’t take long to find an example of how lack of data protection can impact a major organization. In December of 2013, North American retailer Target was subject to a data breach where hackers were able to collect over 40 million credit and debit card numbers as well as 70 million records of Target customers including names, phone numbers, addresses, and emails. This resulted in a 46% drop in profits in the fourth quarter of 2013 compared to that of the year prior, not to mention the $100M spent by Target to increase their security systems let alone conduct damage control.
Another prime example of this issue is that of the recent Ashley Madison hack. For those not familiar, Ashley Madison is an online dating website that allows users to arrange extra-marital affairs. Hackers were able to essentially steal the database user list and went as far as to make the user list publicly available for no other apparent reason outside of disagreeing with what the company represents from an ethical point of view.
Clearly the world has evolved to the point that data is now imperative in order to conduct business. This has resulted in the need for security and protection of this data. Does this protection come from internally generated programs and software or is it best to be licensed out to a third party? What kind of threats should a firm be aware of and where can the best solution be found? This White Paper will explore how data security has evolved in recent years, what kind of solutions are currently available and how the introduction of cloud computing has changed the software security industry in its already short existence.
Size of the Cybersecurity Market
With the use of data growing exponentially so is the need to protect it. Forbes estimates that the worldwide cybersecurity industry totalled $75 billion in 2015 and is projected to grow to $170 billion by 2020. Cybersecurity is a relatively vague term, however it incorporates security measures from technology fields such as the Internet of Things (IoT), fintech and data collection. In fact, IoT related security (included in the original figure) is an industry currently estimated at $6.89 billion and expected to grow to $29 billion by 2020. Cloud security and mobile security are other segments of the market that account for approximately 68% of the market and are projected to grow at 9.8% CAGR by 2020. A testament to how quickly this market is growing is the introduction of cybersecurity insurance – insurance in case of a data breach. Approximately $2.5 billion was spent on this in 2015 and is expected to triple by 2020.
How has the Industry Changed?
There are two major ways companies have had to change their IT infrastructure. They are the result of both innovation and the need for consolidation in an ever growing world of data:
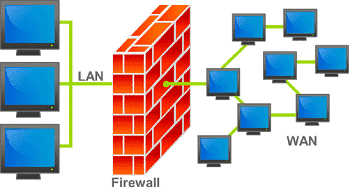 1) Virtualization: This refers to creating virtual platforms rather than having to construct physical ones. Traditionally, companies backed up their information and data into physical hard drives – a practice that is still present today. However, in today’s landscape, this method is only used as a backup in the event that online server space or cloud space fails. Virtualization of server space has allowed companies to eliminate the need for large data centers on premise. While the benefits of virtualization are clear, it has created an additional security concern in the workplace.
1) Virtualization: This refers to creating virtual platforms rather than having to construct physical ones. Traditionally, companies backed up their information and data into physical hard drives – a practice that is still present today. However, in today’s landscape, this method is only used as a backup in the event that online server space or cloud space fails. Virtualization of server space has allowed companies to eliminate the need for large data centers on premise. While the benefits of virtualization are clear, it has created an additional security concern in the workplace.
2) Cloud Computing: Building on the virtualization process, cloud computing is a way to optimize the use of space. Instead of having to store all internal data on large servers at company headquarters, cloud computing provides a virtualized solution for companies to store their data. Essentially, firms lease out space within the cloud (which is offered
by third parties) and have access to the amount of space they need for their data. The essential component of cloud computing is that it allows all parties involved to access the information stored on demand both internally and from remote locations.
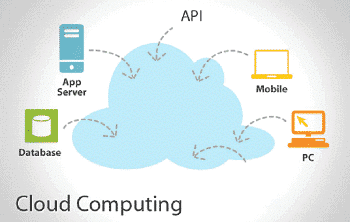 Cloud computing is now at the forefront of infrastructure for both large and small firms alike. As a result, there are numerous considerations being taken regarding its sustainability and practicality in the modern workplace. One important factor is the consideration of Bring Your Own Device (BYOD) in the workplace – a practice that has become more and more commonplace. As well, companies are heavily relying on mobile applications such as Dropbox (a cloud based app) to maintain data within the workforce.
Cloud computing is now at the forefront of infrastructure for both large and small firms alike. As a result, there are numerous considerations being taken regarding its sustainability and practicality in the modern workplace. One important factor is the consideration of Bring Your Own Device (BYOD) in the workplace – a practice that has become more and more commonplace. As well, companies are heavily relying on mobile applications such as Dropbox (a cloud based app) to maintain data within the workforce.
This has resulted in general fear among employees and management regarding the security of apps that are cloud based. According to the Cloud Usage Risk and Opportunities Survey Report by the CSA, which surveyed over 160 IT and security specialists across the U.S., over 50% of respondents stated that the biggest concern about cloud based applications were related to storage. In regards to what policies pertaining to the cloud are most heavily being reinforced, over 80% of respondents indicated that cloud storage and cloud backup were at the forefront, a clear sign that data leakage and security is of the utmost importance.
Types of Security Infrastructures
Perimeter Network Security: One of the more familiar and common security measures is the implementation of firewalls. Firewalls are intended to prevent unauthorized access from unwarranted parties while still allowing the flow of information to and from a company’s network by acceptable parties.
Cloud Security: As we mentioned, cloud computing in the workplace has been on the rise. However, maintaining the integrity of this data and protecting it from unwanted sources is among the biggest problems and fears among users. Cloud computing itself isn’t likely to disappear creating a larger demand for products that can ensure the security of the data contained within the cloud. In fact, 66% of IT specialists say their organization’s use of cloud-based resources reduces their ability to protect confidential information and 64% believe it makes it difficult to secure business critical applications.
Changes & Threats to Firms and the Software They Use
The two examples listed previously are directly indicative of the types of breaches that affect the users of a company’s products or services. However, there is also the matter of protecting a company’s proprietary information as well as the data they use on a daily basis to effectively run their firm. While this data may not have a direct impact on the consumer themselves, it is equally important to the company that this information stay protected.
A recent study attempted to estimate the impact of data breaches on a company in a financial capacity. The study shows that per 100,000 customers, the estimated impact of a data breach is approximately $201.28 per customer totaling $20.1M dollars. With the likelihood of a breach occurring being estimated at 11.8%, the total expected value of a data breach equates to an average of $2.37M. At this point we examine some of the issues related to cybersecurity.
The costliest type of breach that could occur for a company would result from a 50% increase in the backup and storage of customer sensitive data – if this information were lost it would cost a company an average of $7.34M. Another type of costly data breach would result from the expansion of cloud provider operations resulting in financial difficulties (for the provider) – estimated at $7.06M. This point is covered below:
⦁ The access of internal users to external applications warrants the implementation of a security measure. Put simply, this would be a case of an employee going through different websites while at work and the application could be considered the internal database containing company information. Organizations must be able to protect the information stored in the application as well as detect malicious content attempting to enter into it. The standard solution to this problem is the implementations of firewalls. However the ubiquitous use of social media in the workplace has expanded this threat leading to the introduction of Next Generation Firewalls (NGFWs) which provide the same risk management as a traditional firewall but also identifies safe applications while enforcing application-level policies.
⦁ Comparatively, external user access to internal applications is another essential component of data security. This concern directly relates to a company’s bottom line and is in line with the traditional fear of getting hacked. In today’s environment, there are so many users of the data that it is essential to distinguish between users accessing it remotely for legitimate purposes and unwanted viruses or computer hackers. One common fear from this style of attack is known as distributed denial-of-service (DDoS) and it commonly employed as a way of breaching a firm’s data. Solutions must be able to block DDoS attacks and be able to identify legitimate users of the company’s data and malware or attacks that seek to cause harm.
⦁ Bring Your Own Device (BYOD) has become commonplace allowing employees to access sensitive data from their own devices from the workplace and remotely. This results in the most dangerous of breaches should it happen. Approximately 53% of employees use their own devices in the workplace while 50% of this group are connecting to the company cloud via these devices. Inherent in the BYOD problem is that of Bring Your Own Cloud (BYOC) which results from customers bringing third party cloud based apps into the workplace simply as a function of bringing in their own devices.
⦁ Finally, there are risks associated with actually hosting the data through virtualization – essentially in the cloud. As previously mentioned, one of the larger security threats for companies is that of storage management. Access to the cloud must be completely secure to ensure that information is not stolen or contaminated by outside forces such as malware. Due to the size and scale of the data it is essential that latency (i.e. speed) is not an issue and that information is able to quickly and securely flow to and from each necessary party.
Cybersecurity Solutions
As is the nature of such a large industry, there are a growing number of solutions becoming available to meet the cybersecurity needs of everyone from the consumer at home to multinational corporations. Below, we outline the company VirtualArmor, as they are an all-inclusive data security provider.
VirtualArmor (VAI.CSE)
VirtualArmor is an Information Technology company focused on delivering cybersecurity and network solutions to businesses. VirtualArmor partners with leaders in the IT industry to provide solutions and offers the ability to customize a solution based on firm specific needs. Strategic partners include world leaders in the IT security field such as Juniper, IBM, VMware and several others. Solutions include:
⦁ Security Intelligence Solutions: One key to effective information security is visibility – who is accessing what, when, and where; knowing what is normal behavior; identifying abnormal or malicious behavior. In todays enterprise, this visibility typically equates to hundreds of thousands of log entries from network and security devices and platforms, most of which cannot be reviewed in depth. VirtualArmor provides a Security Intelligence platform that will ingest and consume all security and access related data and logs, perform advanced analytics and event correlation across the dataset in real-time, providing the user with a distilled view of identified Security Incidents that are relevant to the specific customer environment and security posture.
⦁ Cloud Application Security Solutions: VirtualArmor offers a Cloud Security and Visibility solution that provides full visibility into usage of cloud applications within an organization, and in many instances provide additional security and audit controls for the applications. This service allows users to securely manage the inflow and outflow of sensitive data from both sanctioned and non-sanctioned cloud apps.
⦁ DDoS Protection Solutions: DDoS are a common form of attacks that firms may face. Over time, these style of attacks have evolved to become better at penetrating security measures and found more creative ways to remain unidentified. VirtualArmor’s DDoS solution protects against the largest and most sophisticated DDoS techniques at the flip of the switch – or automatically when thresholds are exceeded. This solution ensures a company’s critical internet-facing applications and services remain available solely to legitimate users and customers.
While these solutions are a major component of the VirtualArmor suite, they are only a few of the offerings that they provide. Traditionally, companies are forced to work with several third party providers to manage their data security – sometimes several different companies offer solutions to each unique problem. This can be strenuous on a firm’s IT department particularly having to keep track of which service provider resolves which solution. This is inefficient, costly, and time consuming. VirtualArmor acts as an umbrella service provider ensuring that all security measures are covered by one company with 24/7 support while taking advantage of its relationships with strategic partners to ensure the highest quality of protection. These products include:
⦁ Perimeter Network Security: Although the network “perimeter” continues to grow and to blur, traditional and Next Gen (NG) firewalls are still a highly effective first layer of protection. As stated before, these are firewalls that act as a first line of defense against inbound and outbound data both from the office and remotely. As well, the firm’s technology protects against low latency, DDoS attacks and outlines single points of failure immediately.
⦁ Public and Private Cloud Security: Currently a major trend in cybersecurity, VirtualArmor offers a wide variety of solutions to help ensure the security of a company’s public or private cloud. Using virtualization-aware storage solutions and virtualized network functions like secure routers and firewalls hosted in the cloud, VirtualArmor works closely with industry leading partners to ensure the security of the contents within a cloud.
⦁ Remote and Mobile Access: With individual mobile devices and working away from the office becoming commonplace in the workforce, the security of remote access and mobile devices has never been more important. VirtualArmor is able to work closely with any company’s IT departments to ensure that remote access has low-latency and that there is minimal risk from employees accessing sensitive material from their remote devices or outside the office.
Conclusion
As we can see, cybersecurity and data management has become an increasingly growing concern for companies of all sizes. The introduction of cloud based computing has entirely shifted the paradigm of thinking for companies across the world. Data management is now at the forefront of the minds of companies that seek to maintain productivity in this new digital age as well as keep information out of the hands of those seeking to cause harm. The Target leak and Ashley Madison leak are only two of countless examples of businesses being taken advantage of and they both go to show the damage that can be done from both a financial perspective and reputation perspective. These examples are two of many that have already occurred and without a doubt there will be many more to come. As data security strengthens, hackers and ill-intentioned groups find new ways to gain access to information and cause harm. As businesses and consumers continue to navigate their way in a digital economy, cybersecurity will play an ever increasing role in ensuring that safety of all parties involved.
About Virtus Advisory Group
Virtus Advisory Group is an independent capital markets advisory firm, providing select private and publicly listed companies with capital markets strategy, investor relations and business consulting services. We specialize in helping technology, healthcare and clean energy companies strategically navigate the capital markets, grow retail and institutional investor base and effectively communicate with all stakeholders.
Disclaimers
The information and recommendations made available here by The Virtus Advisory Group Inc. (“Virtus Advisory”) and/or all affiliates is for information purposes only. The opinions expressed in this article are based upon our analysis and interpretation of widely available market and company information, and not to be used or construed as an offer to sell or solicitation of an offer to buy any services or securities. Virtus Advisory nor its principals, officers, directors, representatives, and associates will be liable for the accuracy of the information included in this article nor shall be liable for any losses or liabilities that may be occasioned as a result of the information or commentary provided in this article. Virtus Advisory may act as capital markets advisor for certain or all of the companies mentioned in this article, and may receive remuneration for its services. Virtus Advisory and/or its principals, officers, directors, representatives, and associates may have a position in the securities mentioned in this article and may make purchases and/or sales of these securities from time to time in the open market or otherwise. Do not consider buying or selling any stock without conducting your own due diligence. Prior to making any investment decision, it is recommended that you seek outside advice from a qualified or registered investment advisor.
Leave a Reply
You must be logged in to post a comment.



 Share
Share Tweet
Tweet Share
Share




Comment